A simple spreadsheet can articulate what content and display patterns go on a given page while describing their… | Spreadsheet, Spreadsheet template, Design system

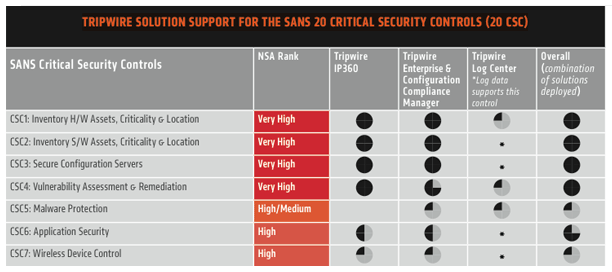
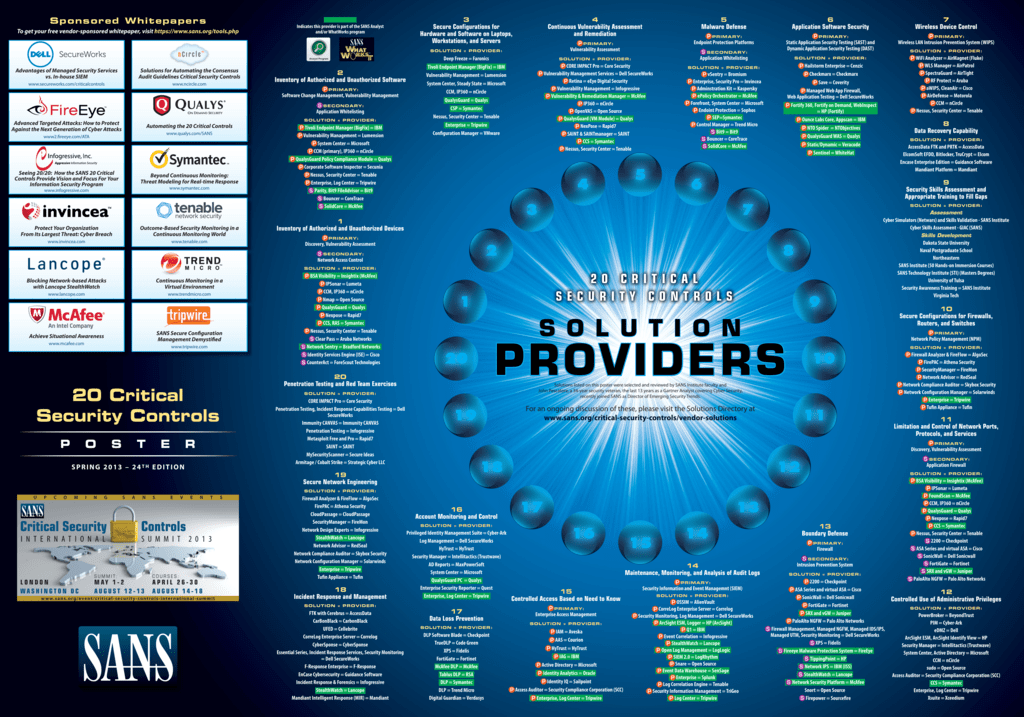
Twitter \ Michael Fisher على تويتر: "What are the top 20 controls for a healthy network #Security posture? {Infographic} #CyberSecurity #infosec #education #DevOps #Malware #databreach #Pentesting #IRP https://t.co/drouJDCjhL"