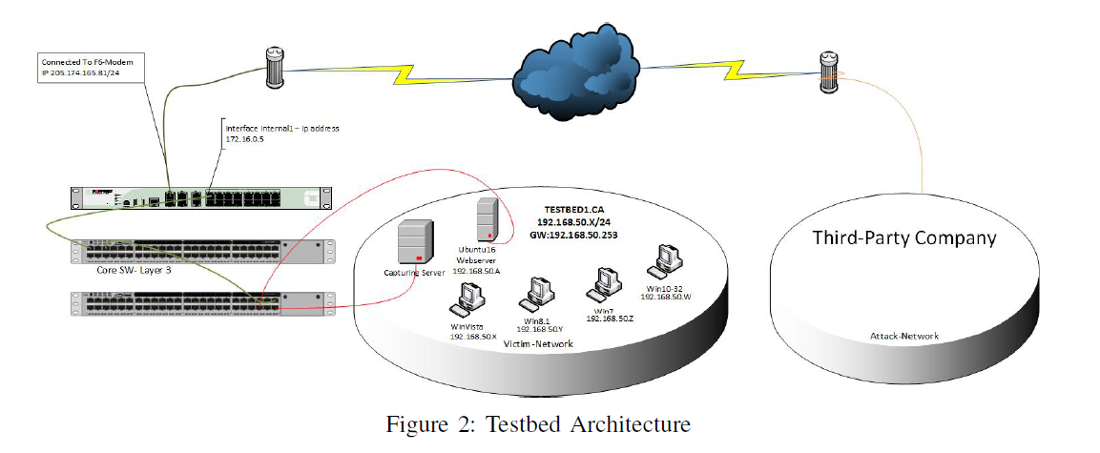
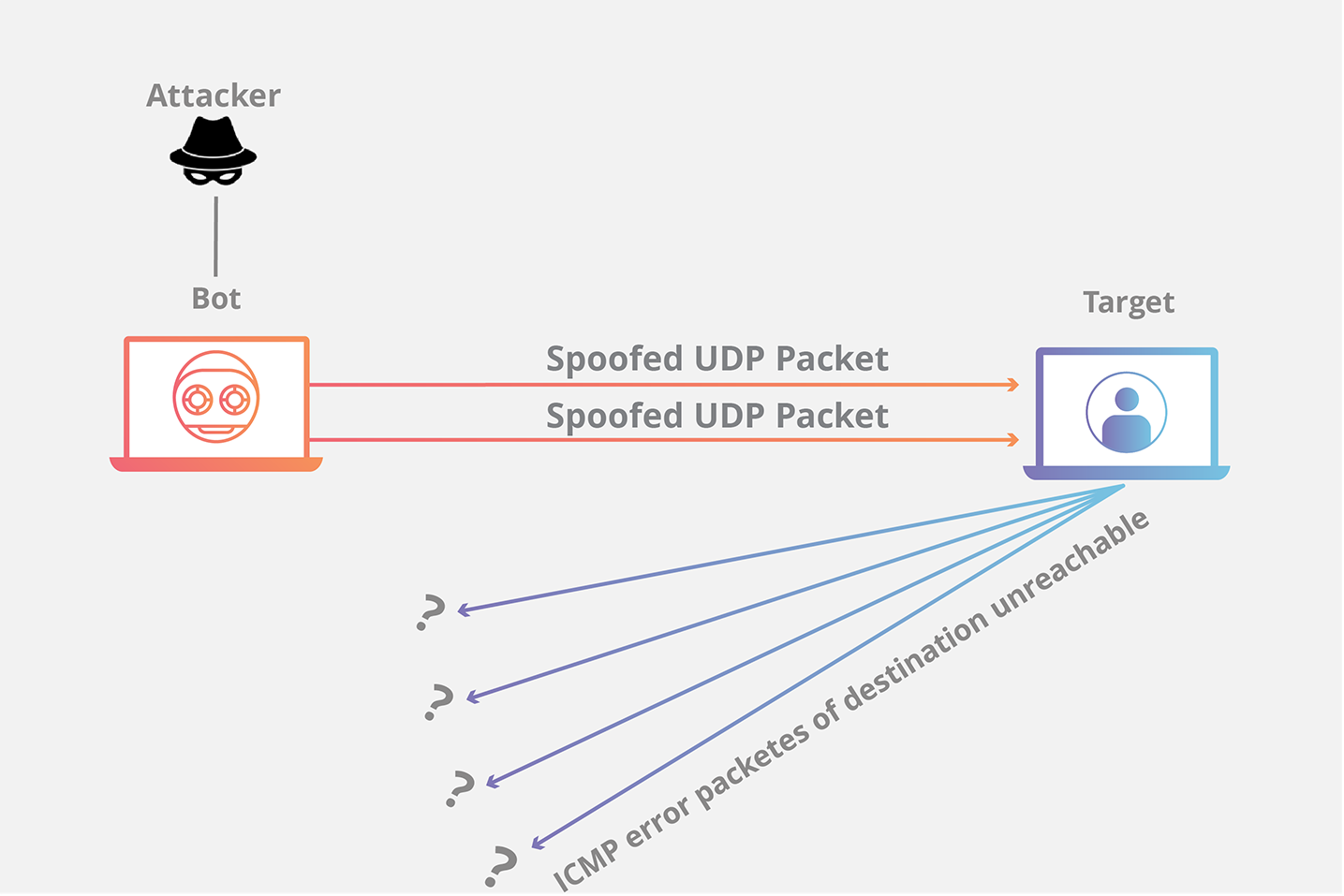
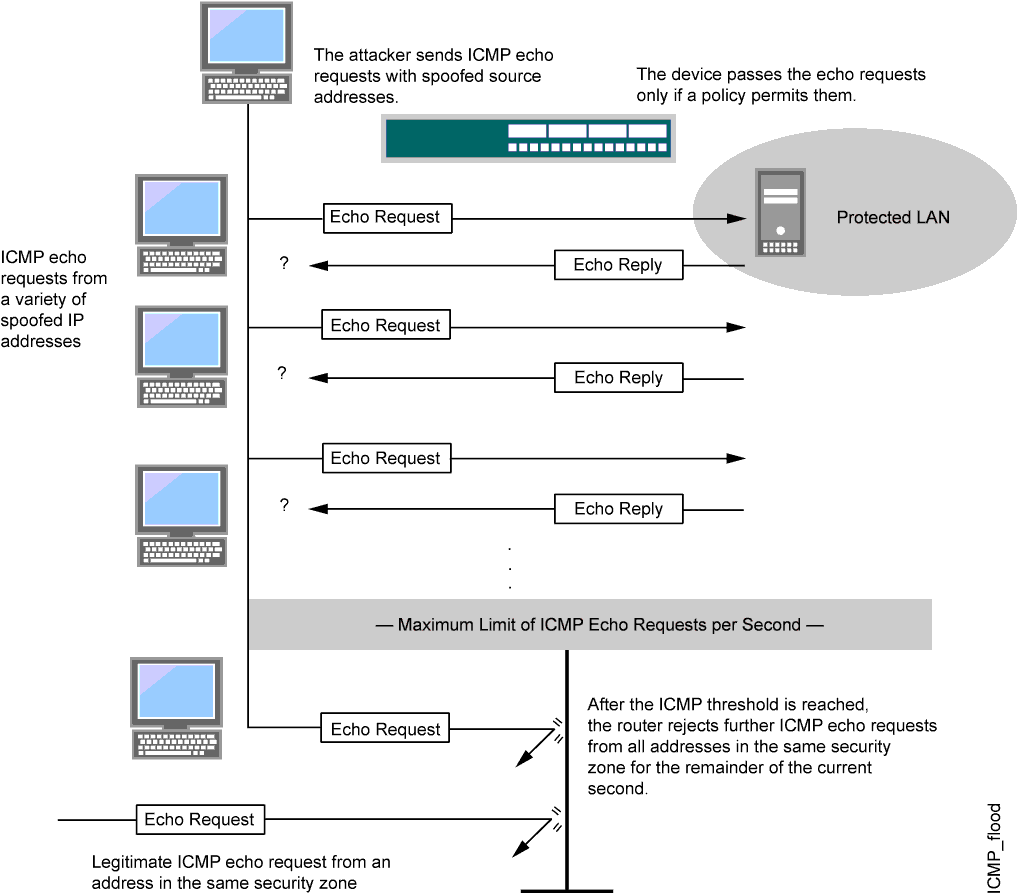
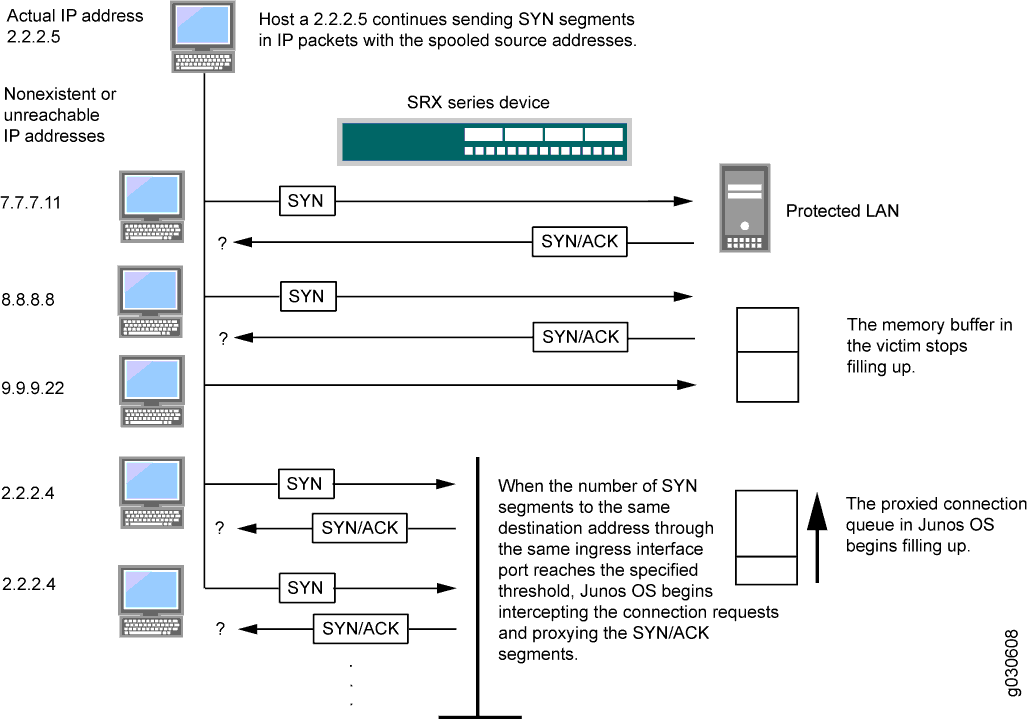
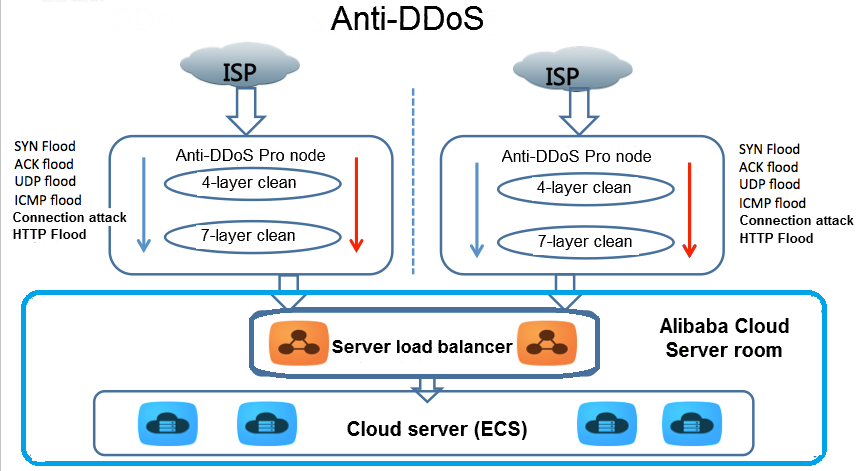
How do threat logs look like if UDP flood detected by Classifie... - Knowledge Base - Palo Alto Networks

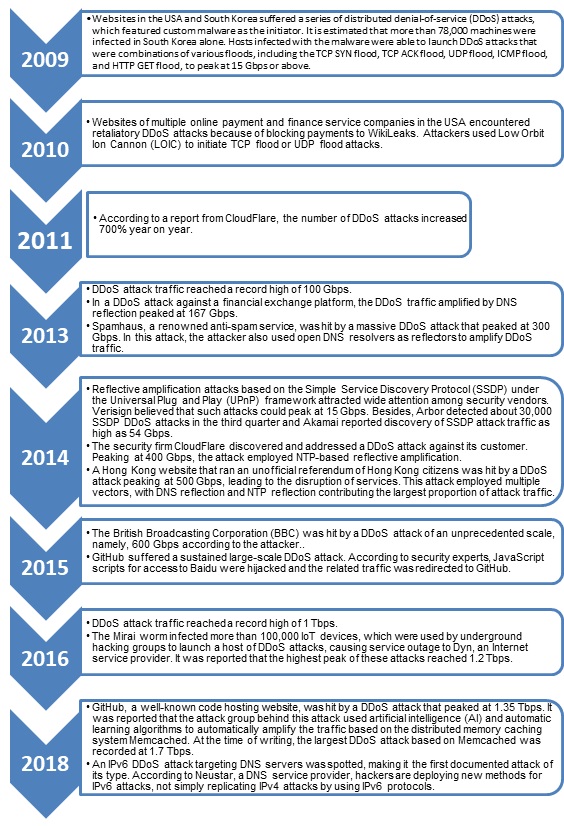
Basic UDP Flood Attack. DDOS and Anti-DDOS methods. Articole introductive si ajutor | Evidweb Network

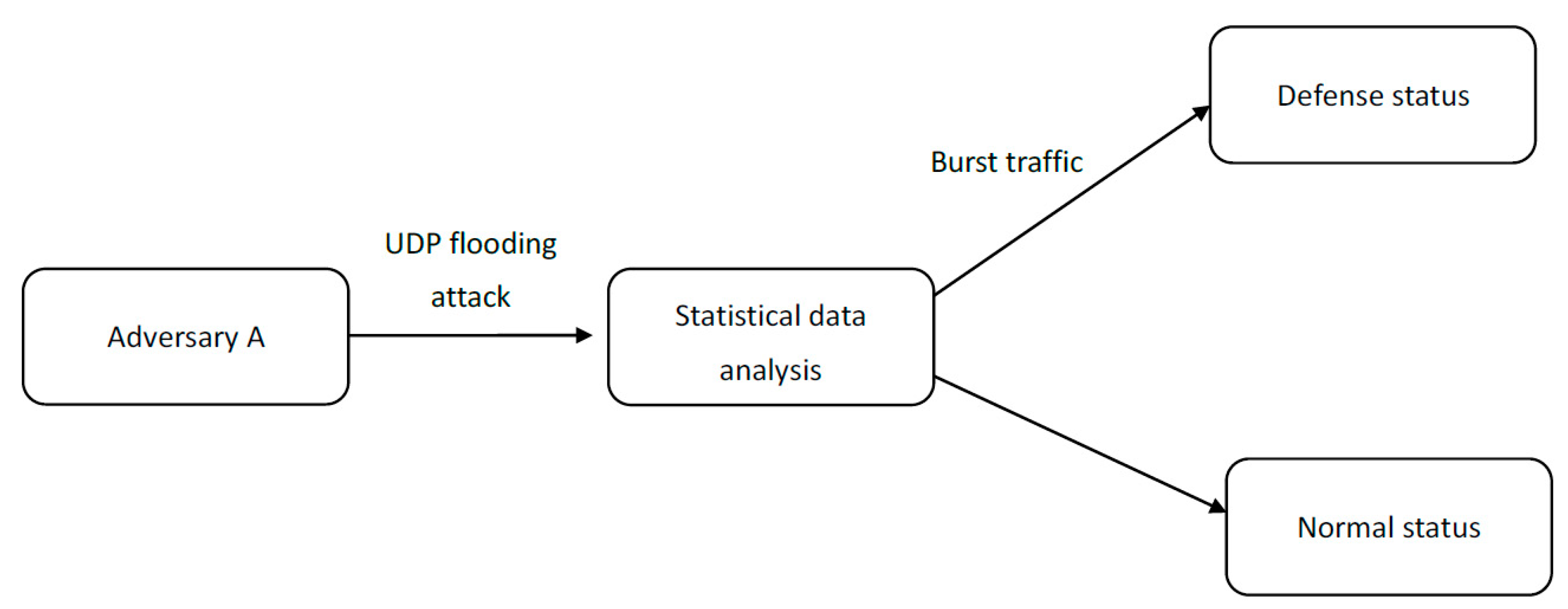
Lightweight Statistical Approach towards TCP SYN Flood DDoS Attack Detection and Mitigation in SDN Environment
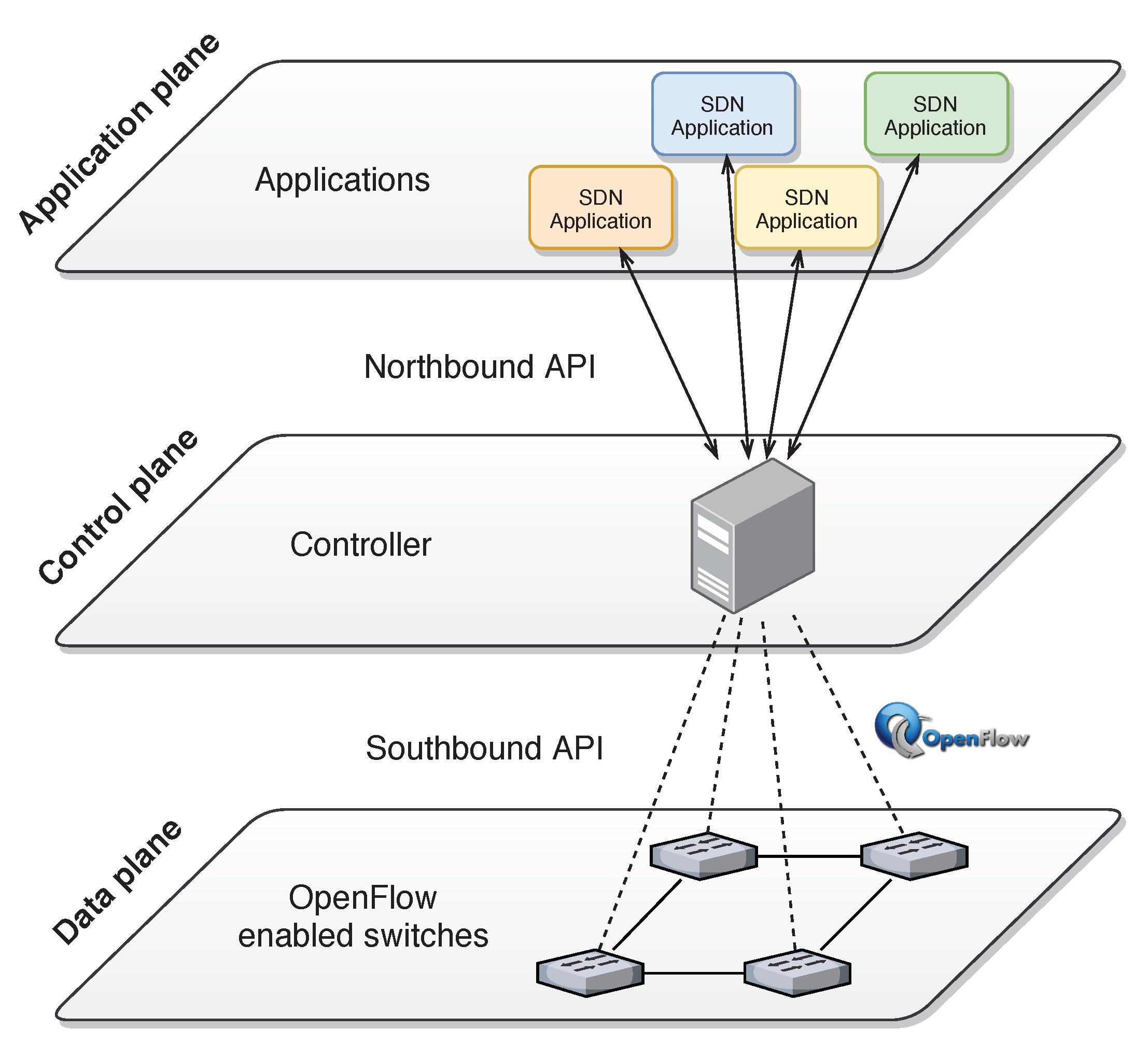
Sensors | Free Full-Text | Detection and Mitigation of DoS and DDoS Attacks in IoT-Based Stateful SDN: An Experimental Approach


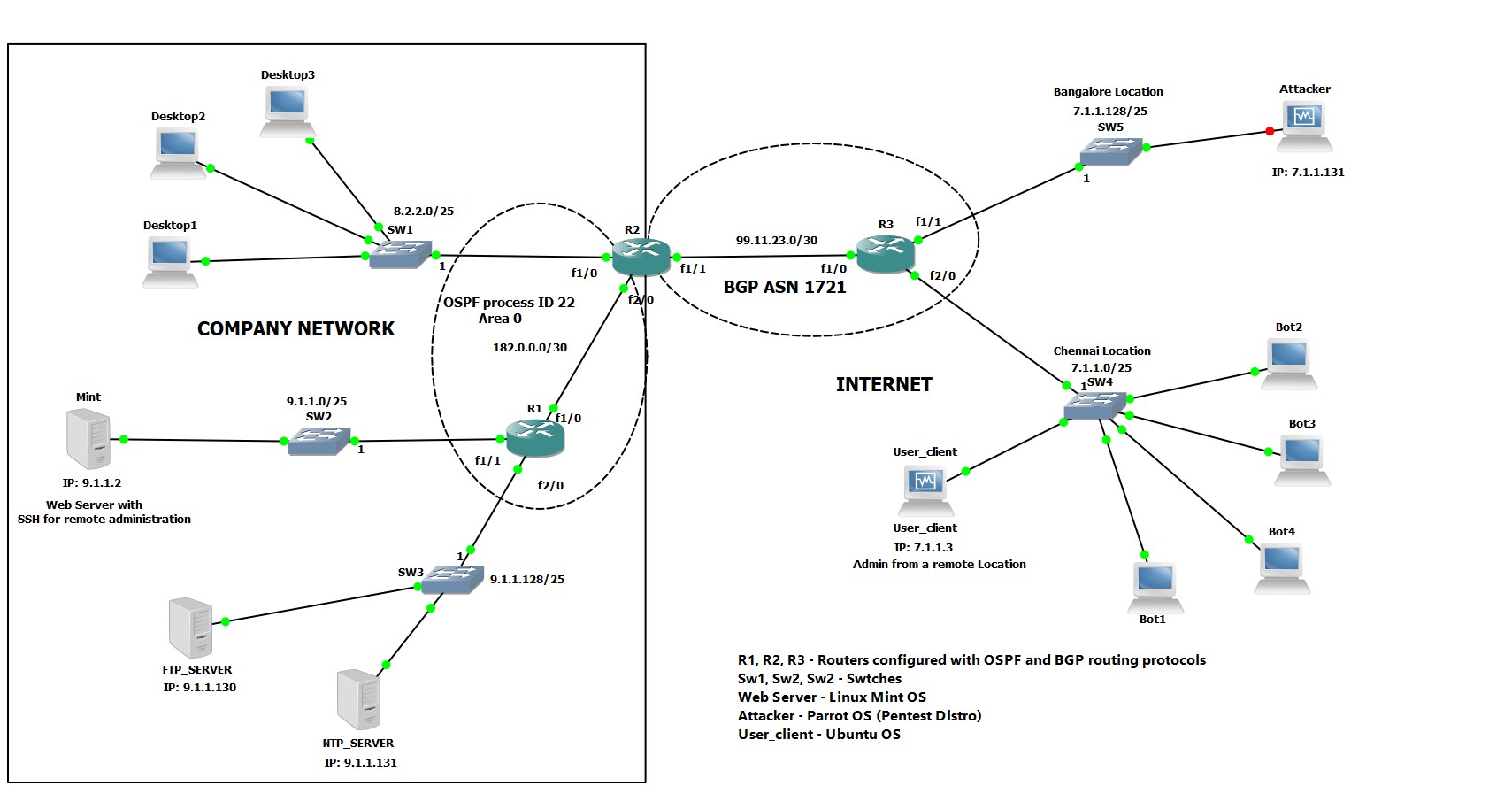
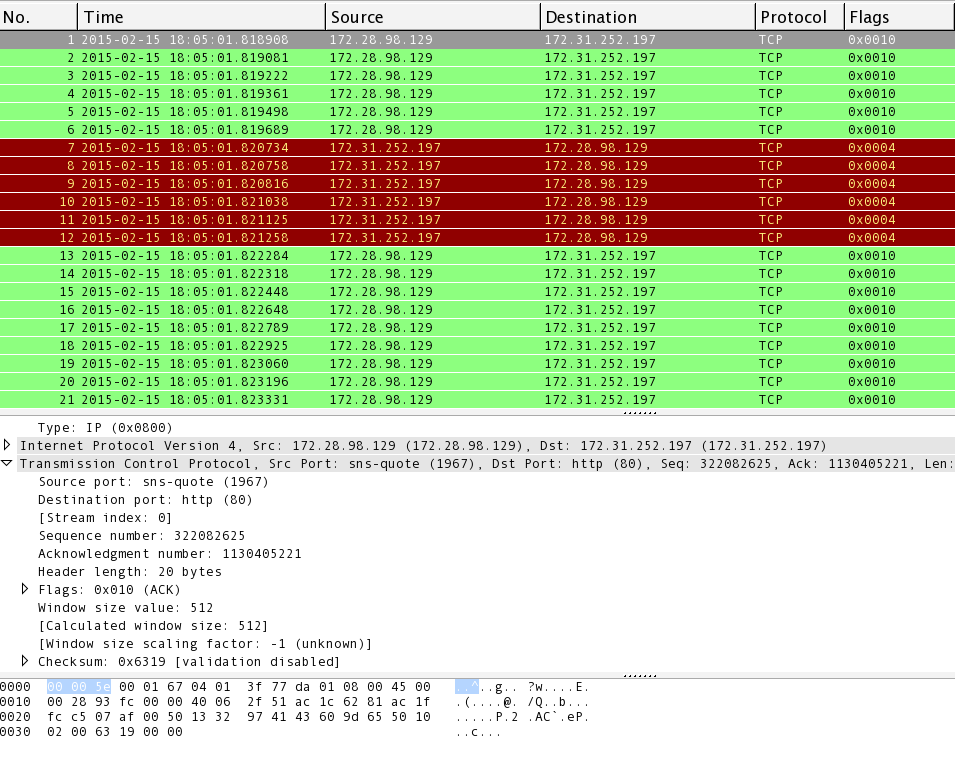

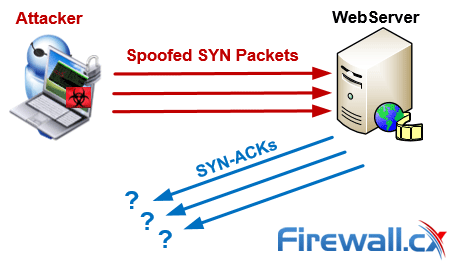

![Real-time DDoS flood attack monitoring and detection (RT-AMD) model for cloud computing [PeerJ] Real-time DDoS flood attack monitoring and detection (RT-AMD) model for cloud computing [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2022/cs-814/1/fig-3-full.png)