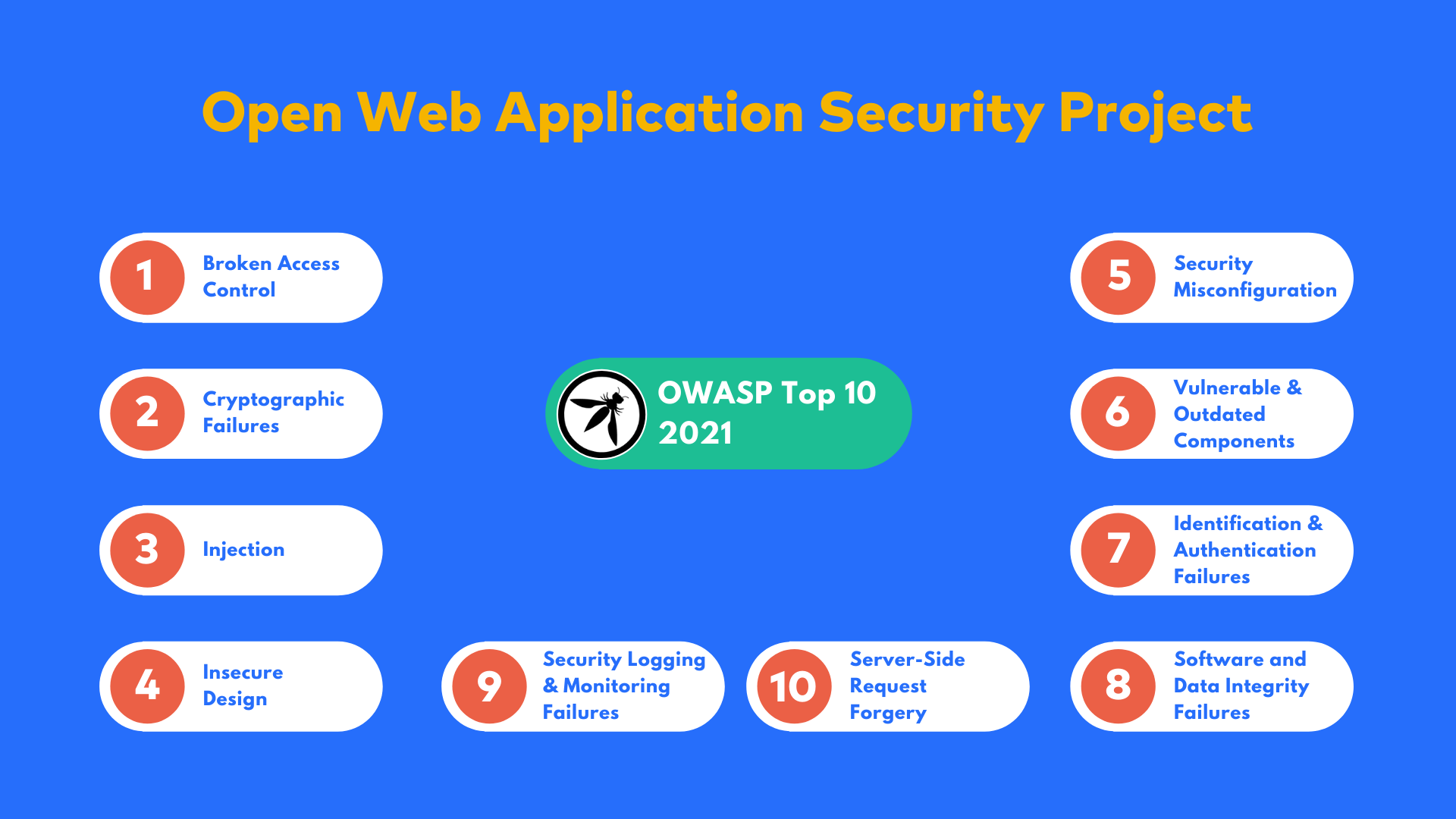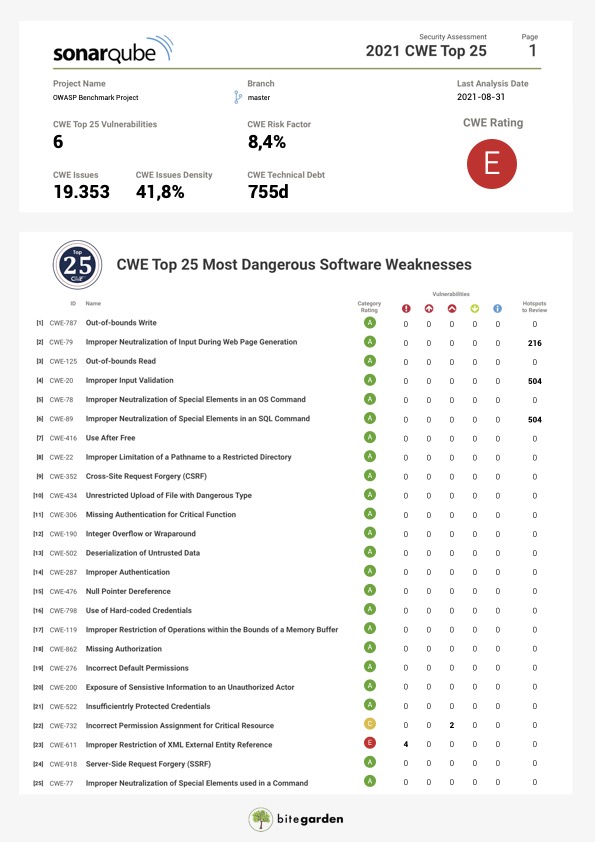
CWE Top 25 2021 now included in the Security Plugin for SonarQube | bitegarden - Plugins for SonarQubeTM
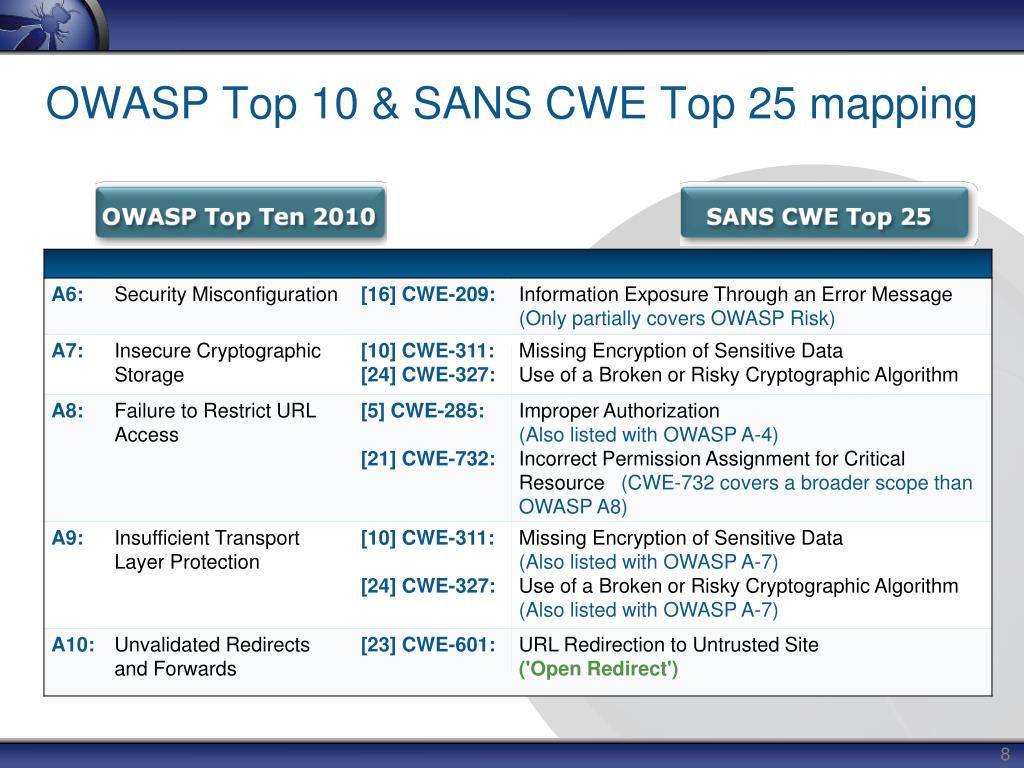
PPT - 2010 CWE/SANS Top 25 with OWASP Top 10 and PCI DSS V2 Mapping PowerPoint Presentation - ID:5764950
![PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/60a3c8428275b406759783c67c2b1d81e8ae6050/4-Table2-1.png)
PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar
![PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/60a3c8428275b406759783c67c2b1d81e8ae6050/3-Figure1-1.png)
PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar
![PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/60a3c8428275b406759783c67c2b1d81e8ae6050/4-Table1-1.png)
PDF] Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST) | Semantic Scholar

PPT - 2011 CWE/SANS Top 25 with OWASP Top 10 and PCI DSS V2 Mapping PowerPoint Presentation - ID:2504152
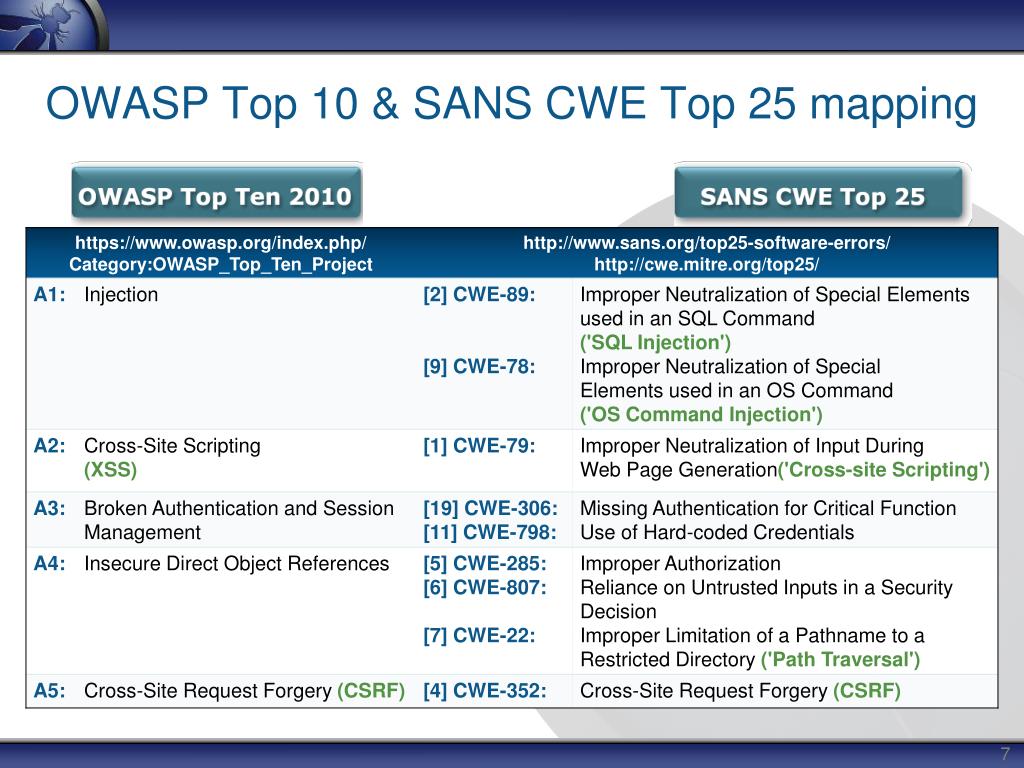
PPT - 2010 CWE/SANS Top 25 with OWASP Top 10 and PCI DSS V2 Mapping PowerPoint Presentation - ID:5764950

SCFM: Secure Coding Field Manual: A Programmer's Guide to OWASP Top 10 and CWE/SANS Top 25: Wear, Sunny: 9781508929574: Amazon.com: Books

PDF) Vulnerabilities Mapping based on OWASP-SANS: a Survey for Static Application Security Testing (SAST)